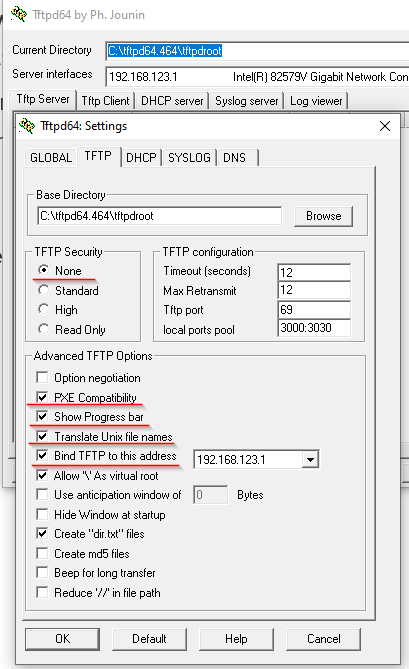
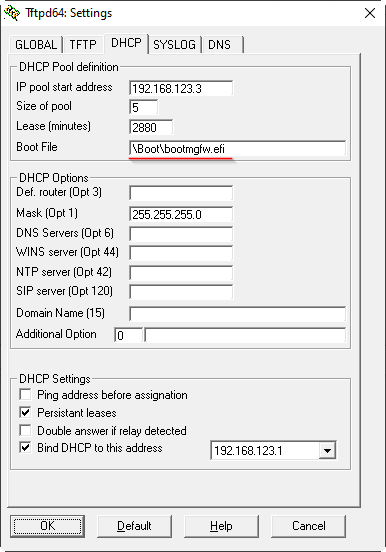
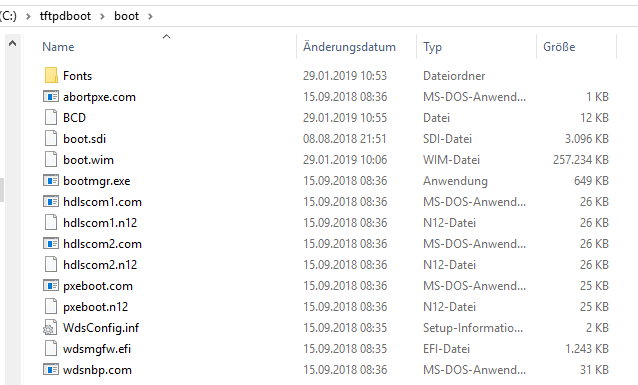
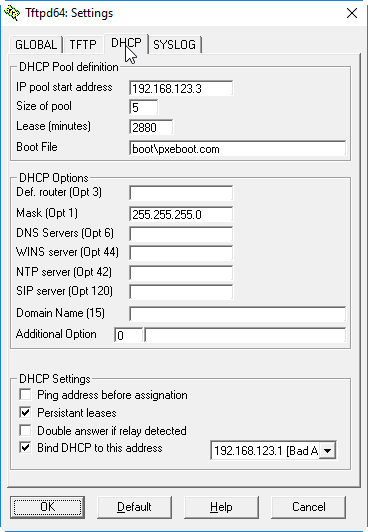
Ubuntu laut Anleitung vorbereitet und gebootet. Updates abwarten (20 Min etwa)
https://jamesachambers.com/raspberry-pi-4-ubuntu-20-04-usb-mass-storage-boot-guide/
mit
locales
die sprache prüfen
mit
sudo dpkg-reconfigure locales
die Sprache ändern
neuen benutzer einrichtensudo adduser
benutzer zu sudo hinzufügensudo usermod -aG sudo
teste ob user wirklich sudo rechte hat. werde zu neuem user
sudo su
<benutzername>: sudo whoami #sollte roote ausgebenalten ubuntu user löschen
sudo userdel -R ubuntu
verschlüsselte festplatte
installiere udisks
sudo apt install udisks2
sudo udisksctl unlock -b <disk>firewall
prüfen ob aktiv
sudo ufw status
ssh erlauben
sudo ufw allow ssh
http erlauben
sudo ufw allow http
sudo ufw allow https
ufw bei systemstart mitstarten
sudo ufw enable
hostname ändern
sudo nano /etc/hosts
sudo nano /etc/hostname
sudo hostname -F /etc/hostname
apache2 installieren
sudo apt install apache2
sudo nano /etc/apache2/apache2.conf
ServerSignature Off
ServerTokens Prod
SSLProtocol -ALL +TLSv1.2
SSLCipherSuite ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUMmod_rewrite
sudo a2enmod rewrite
a2enmod proxy
a2enmod proxy_http
a2enmod ssl
cerbot
sudo apt install certbot python3-certbot-apache
emby
https://emby.media/linux-server.html
curl -L –out emby.deb
sudo dpkg -i emby.deb
htop
sudo apt install htop
samba
sudo apt install samba
Ports 139 und 445 freigeben in der Firewall
sudo ufw allow from 192.168.178.0/24 to any port 139
sudo ufw allow from 192.168.178.0/24 to any port 445
smb.conf:
[Public]
create mask = 0775
directory mask = 0775
force group = users
guest ok = Yes
path = /mnt/nas/Public
write list = arne
[Arne]
create mask = 0770
directory mask = 0770
force group = arne
force user = arne
path = /mnt/nas/Arne
read only = No
valid users = arne
samba user erstellen
sudo smbpasswd -a <username>
ssh
enable public key
ggf public key aus private key erstellen
ssh-keygen -f <pfad/zum/privatekey> -y > public_key
ddclient für dynv6
sudo apt install ddclient
config laut dynv6, username auch wirklich none eingeben
nextcloud
sudo apt install mariadb-server php7.4-bcmath php7.4-bz2 php7.4-cli php7.4-common php7.4-curl php7.4-gd php7.4-json php7.4-mbstring php7.4-mysql php7.4-xml php7.4-zip php7.4 php7.4-fpm php7.4-intl
datenbank und user in mariadb anlegen
create database nextcloud;
CREATE USER ’nexcloud’@’localhost‘ IDENTIFIED BY ‚changeme‘;
GRANT ALL PRIVILEGES ON nextcloud.* TO ’nextcloud’@’localhost‘;
FLUSH PRIVILEGES;
exit;
php.ini
sudo nano /etc/php7.4/fpm/php.ini
memory_limit = 512M
output_buffering = off
fail2ban
für emby
/etc/fail2ban$ sudo nano filter.d/emby.conf
[Definition]
failregex = AUTH-ERROR: – Invalid user
HTTP Response 401 to .
/etc/fail2ban$ sudo nano jail.d/emby.local
[emby]
enabled = true
filter = emby
logpath = /var/lib/emby/logs/embyserver.txt
port = 80,443
für nexcloud
Create a file in /etc/fail2ban/filter.d named nextcloud.conf with the following contents:
[Definition]
_groupsre = (?:(?:,?\s*"\w+":(?:"[^"]+"|\w+))*)
failregex = ^\{%(_groupsre)s,?\s*"remoteAddr":"<HOST>"%(_groupsre)s,?\s*"message":"Login failed:
^\{%(_groupsre)s,?\s*"remoteAddr":"<HOST>"%(_groupsre)s,?\s*"message":"Trusted domain error.
datepattern = ,?\s*"time"\s*:\s*"%%Y-%%m-%%d[T ]%%H:%%M:%%S(%%z)?"
The jail file defines how to handle the failed authentication attempts found by the Nextcloud filter.
Create a file in /etc/fail2ban/jail.d named nextcloud.local with the following contents:
[nextcloud]
backend = auto enabled = true port = 80,443 protocol = tcp filter = nextcloud maxretry = 3 bantime = 86400 findtime = 43200 logpath = /path/to/data/directory/nextcloud.log
lüfterscript einbauen
hd-idle
sudo nano /etc/default/hd-idle
START_HD_IDLE=true
HD_IDLE_OPTS=“-i 1800 -a /dev/disk/by-uuid/9ffe642b-6af8-49b3-952f-2c86f1f3b37f -i 1800 -a /dev/disk/by-uuid/369dda9c-0411-4ddd-a630-eed8d66b941e -l /var/log/hd-idle.log“ -a /dev/disk/by-uuid/82b8afee-51f5-43e9-bb35-7e108f073c3d -a /dev/disk/by-uuid/d89ada69-30a4-405c-b2f9-532fce8d0078 -l /var/log/hd-idle.log“
sudo systemctl enable hd-idle
sudo systemctl start hd-idle
mailversandt
sudo usermod -aG mail <benutzername>
dann ab und wieder anmelden
sudo apt install mailutils
als satelit einrichten
sudo nano /etc/postfix/main.cf
(vorhandenes smtp_tls_security_level auskommentieren)
smtp_sasl_auth_enable = yes
smtp_sasl_security_options = noanonymous
smtp_sasl_password_maps = hash:/etc/postfix/sasl_password
sender_canonical_maps = hash:/etc/postfix/sender_canonical
smtp_tls_security_level = encrypt
virtual_alias_domains = nas
virtual_alias_maps = hash:/etc/postfix/virtual
sudo touch /etc/postfix/sasl_password
sudo nano /etc/postfix/sasl_password
mail.gmx.net mail_adresse@gmx.de:passwort
sudo nano /etc/postfix/sender_canonical
www-data meine_adresse@gmx.de
root meine_adresse@gmx.de
arne meine_adresse@gmx.desudo postmap hash:/etc/postfix/sasl_password
sudo postmap /etc/postfix/sender_canonical
sudo nano /etc/postfix/virtual
@example.com example@gmx.de
sudo postmap /etc/postfix/virtual
sudo systemctl restart postfix
zumtesten:echo Hallo! dies ist ein Test! | mail -s Testmail meine_adresse@gmx.deAuto Updates
sudo apt install unattended-upgrades apt-listchanges
sudo dpkg-reconfigure -plow unattended-upgrades
sudo nano /etc/apt/apt.conf.d/50unattended-upgrades
Die Zeile //Unattended-Upgrade::Mail ""; suchen und auskommentieren und mit eurer E-Mailadresse ergänzen.
Unattended-Upgrade::Mail „info@beyond.lol“;
Für den automatischen Neustart folgende Zeilen anpassen
//Unattended-Upgrade::Automatic-Reboot „false“;
Unattended-Upgrade::Automatic-Reboot „true“;
//Unattended-Upgrade::Automatic-Reboot-Time „02:00“;
Unattended-Upgrade::Automatic-Reboot-Time „02:00“;
sudo unattended-upgrades –dry-run